Connect to Ping Identity
Last updated December 6th, 2023
Ping Identity provides services for user identity and authentication based on System for Cross-domain Identity Management (SCIM) 2.0 and OpenID Connect (OIDC) protocol.
You can integrate and connect Knox Manage with Ping Identity services to manage user authentication across your enterprise applications. The integration is enabled by the cloud-based Knox Manage MDM app on the Ping Identity portal. When connected and configured, the user and group information in your Ping Identity tenant is synced with Knox Manage.
Consider the following while integrating with Ping Identity:
-
Syncing of organizations isn’t currently supported.
-
User authentication is executed directly by Ping Identity.
-
Multi-factor authentication (MFA) is supported and set up in the Ping Identity portal. Knox Manage follows the MFA set up in Ping Identity.
-
SCIM setting is required to enable user provisioning and synchronization.
- Make note of the tenant URL and secret token information before saving your settings in the Ping Identity portal. You can only renew this information after the settings are saved.
-
OIDC setting is required to enable user authentication. You can configure OIDC before SCIM, or after SCIM is set and user information sync is successful.
Connect Knox Manage to Ping Identity through OIDC
To connect Knox Manage with Ping Identity for user authentication using the OIDC configuration:
-
Access the Ping Identity console, navigate to Connections > Applications > Add Application, and add the Knox Manage app as a Single-Page application type. The OIDC app for Knox Manage is added to the list of applications in the console.
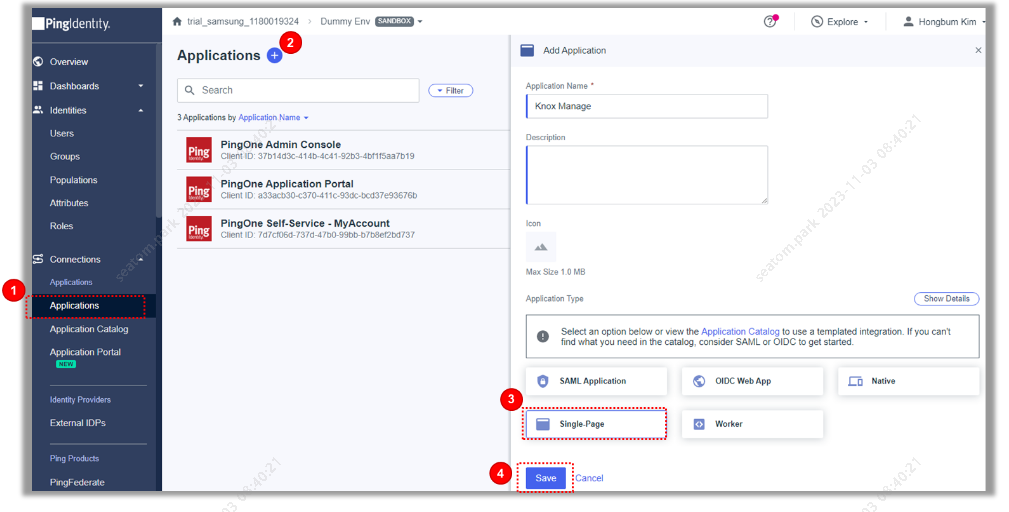
-
Select the Knox Manage app from the application list and click OpenID Connect Edit to edit the configuration.
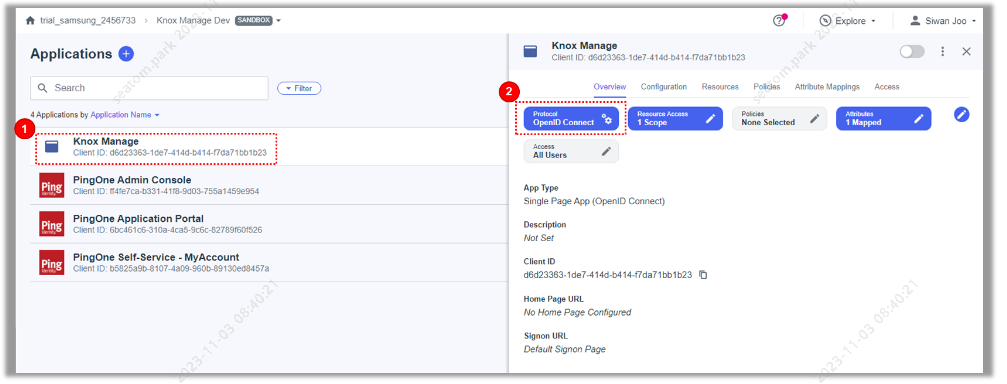
-
Enter and save CRS callback information under Response Type (Code, Token, ID Token selection), Grant Type (Authorization Code, Implicit selection), and Redirect URIs, and click Save.
Ensure the CRS information in Sign-in redirect URIs is correct to avoid errors during user authentication. Enter the following URI for Knox — https://crs.manage.samsungknox.com/crs/auth/callback.
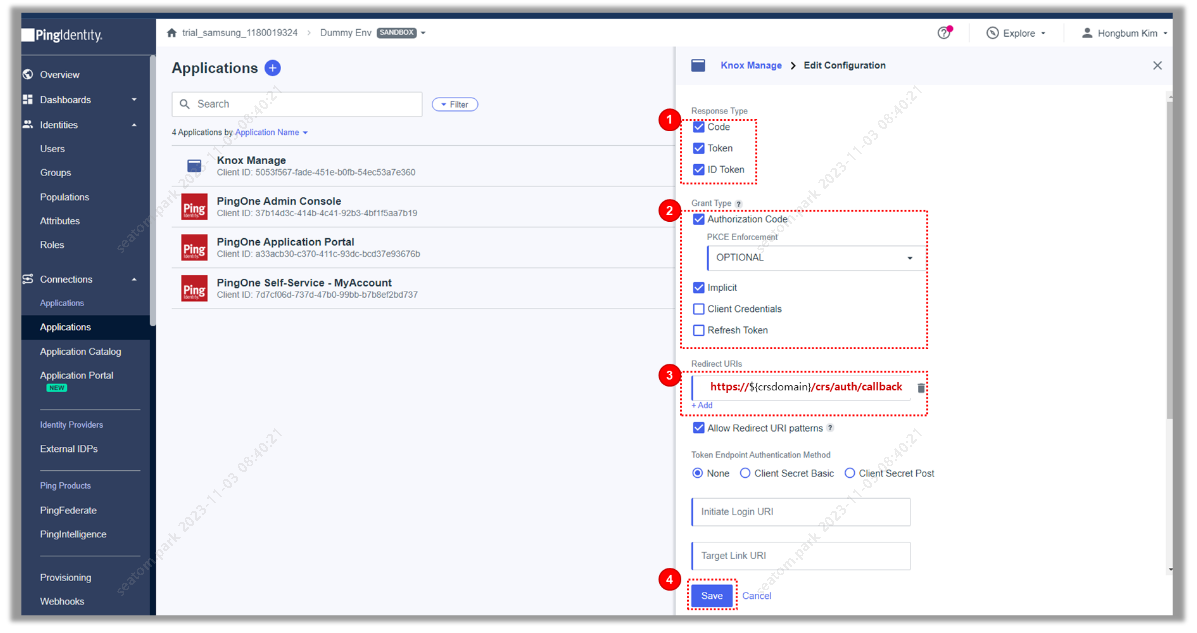
-
After saving the configuration, go to the Policies tab and click Add Policies to add single and multi factor authentication policies. Depending on the option defined, a policy is determined when signing in a user.
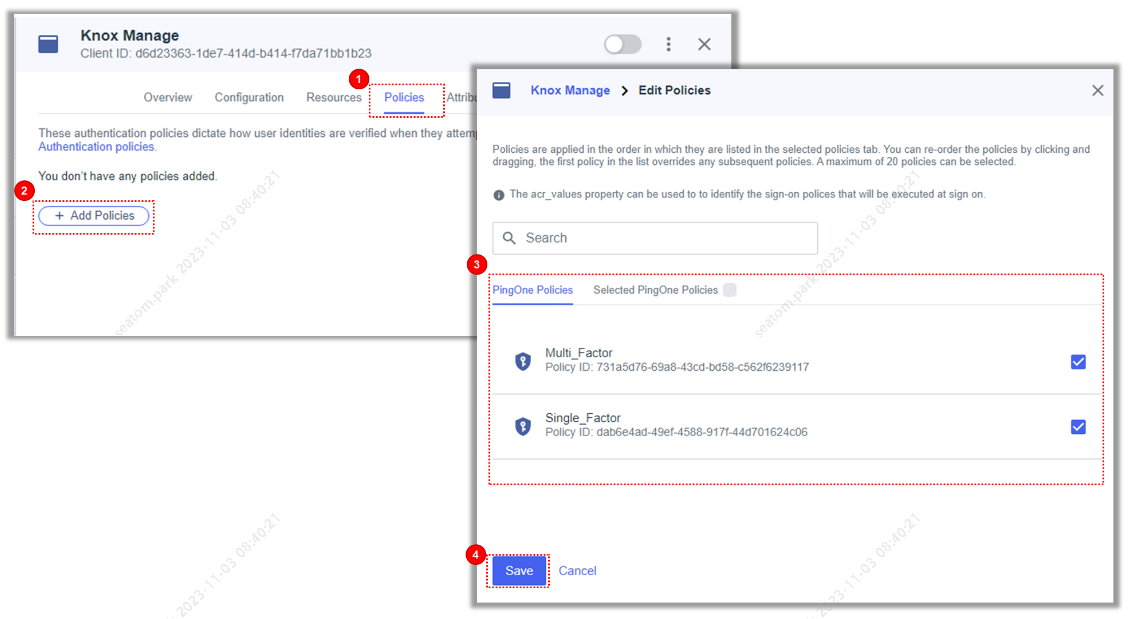
-
Enable the Knox Manage app using the toggle at the top.
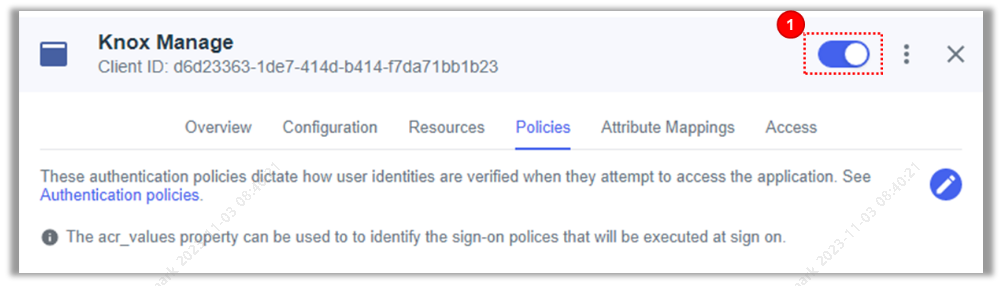
-
In the Configuration tab, copy and save the values of Client ID and OIDC Discovery Endpoint. These values are required for configuring Knox Manage OIDC settings.
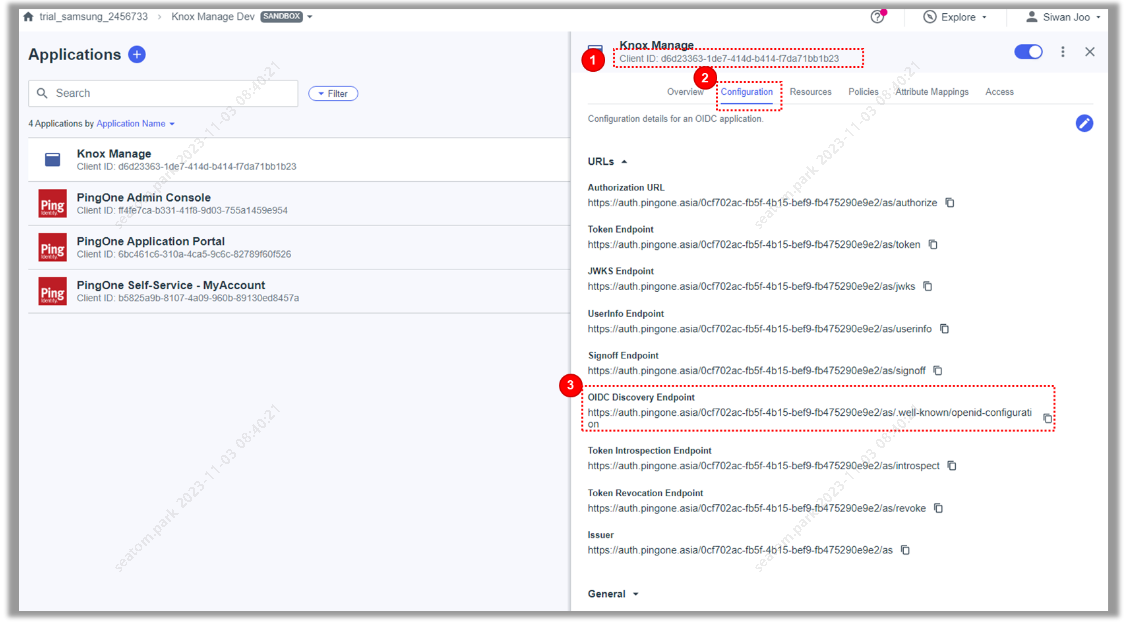
-
(Optional) To perform MFA testing with a user, enable the MFA setting in the Ping Identity console.
If no other MFA is set up, the MFA available in the PingID app is used by default.
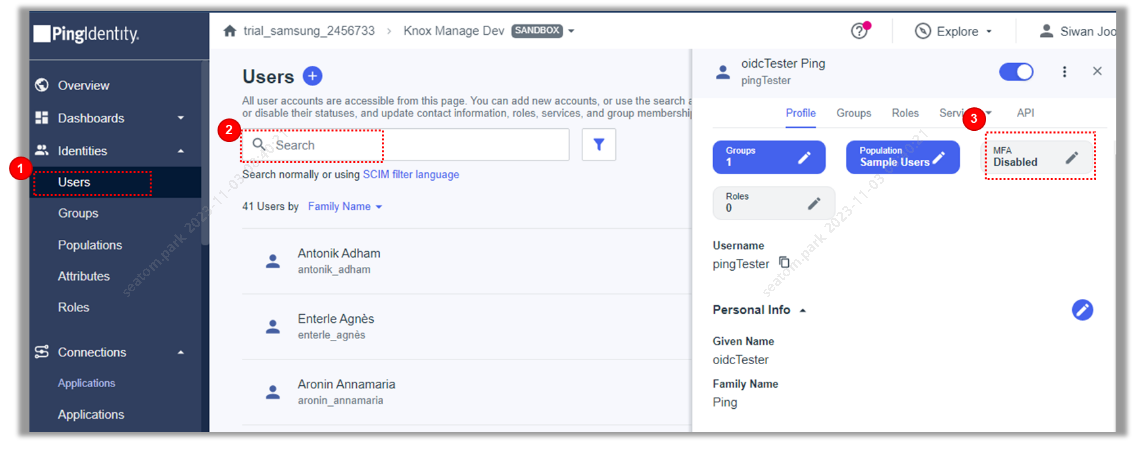
-
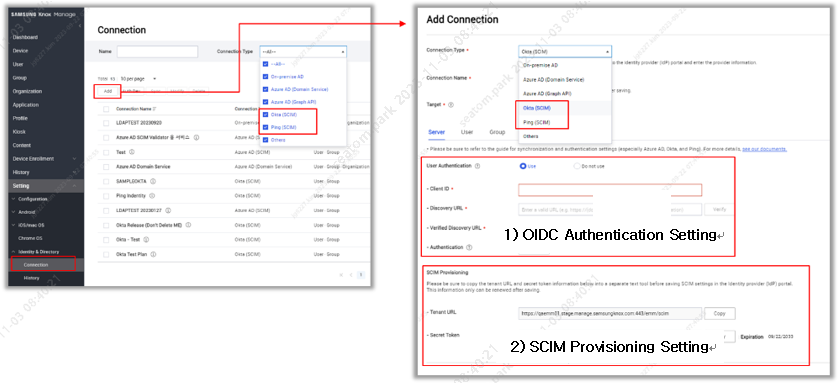
On the Knox Manage Console, go to Setting > Identity & Directory > Connection > Add Connection, and integrate Ping Identity OIDC authentication as follows:
-
Select Okta (SCIM) for Connection Type
-
Select Use for User Authentication
-
Enter the previously copied Ping Identity OIDC client ID in the Client ID field
-
Enter the previously copied Ping Identity OIDC metadata URI in the Discovery URL field.
All SCIM settings must be completed in one go. Refer to the following section for details.
If you set user authentication as Do not use, OIDC authentication must be configured after the SCIM provisioning is set and the sync for device enrollment is successful.
-
Connect Knox Manage to Ping Identity through SCIM for automatic user provisioning
To enable automatic user provisioning, you must configure settings in the Knox Manage console and in the Ping Identity console.
Once configured, Ping Identity automatically provisions and de-provisions users and groups to Knox Manage using the Ping Identity provisioning service. The following capabilities are supported:
-
Creation of users and groups in Knox Manage
-
Deactivation or deleting of users in Knox Manage when they do not require access anymore
-
Sync of user attributes between Okta and Knox Manage
-
Provisioning of groups and group memberships in Knox Manage
Prerequisites
-
A Ping Identity Organization
-
A Knox Manage tenant
-
A user account in Ping Identity with roles to configure provisioning (such as Client Application Administrator, Client Application Developer, or Organization Administrator)
-
A Knox Manage user account with admin permission
Step 1 — Configure Knox Manage to support provisioning with Ping Identity
-
Sign in to the Knox Manage console.
-
Go to Setting > Identity & Directory > Connection and click Add.
-
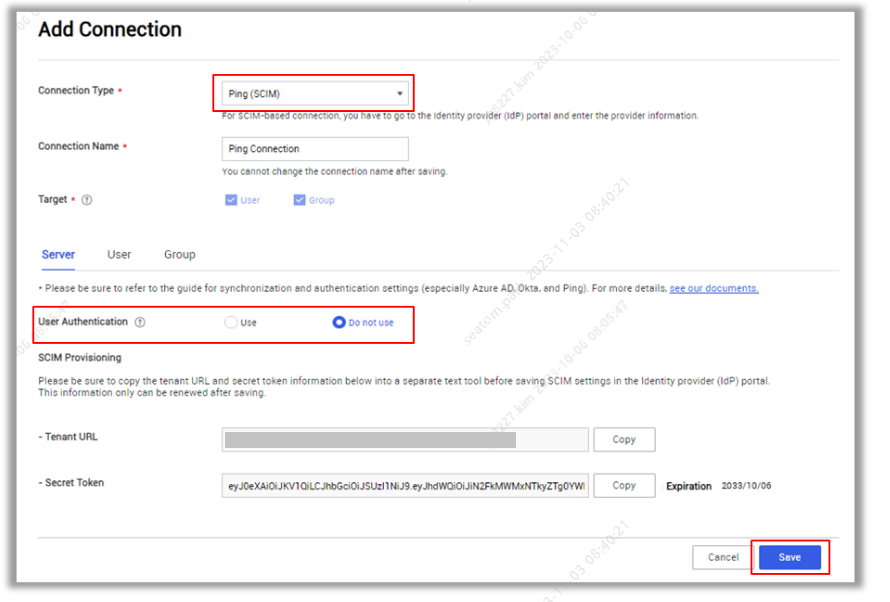
On the Add Connection page, set Connection Type as Ping (SCIM).
-
Copy the Tenant URL and Secret Token and ensure to keep them accessible for later use in the Ping Identity portal. The secret token cannot be retrieved, it can only be reissued.
-
If you completed OIDC setup on the Ping Identity tenant, enter Client ID and Discovery URL. Ensure that Do not use is selected for User Authentication.
-
You can set user authentication after setting up SCIM.
-
-
Click Save.
Step 2 — Configure automatic user provisioning for Knox Manage
You can configure the Ping Identity provisioning service to create, update, and disable users in Knox Manage based on user assignments defined in Ping Identity.
To configure connection for Samsung Knox Manage in Ping Identity:
-
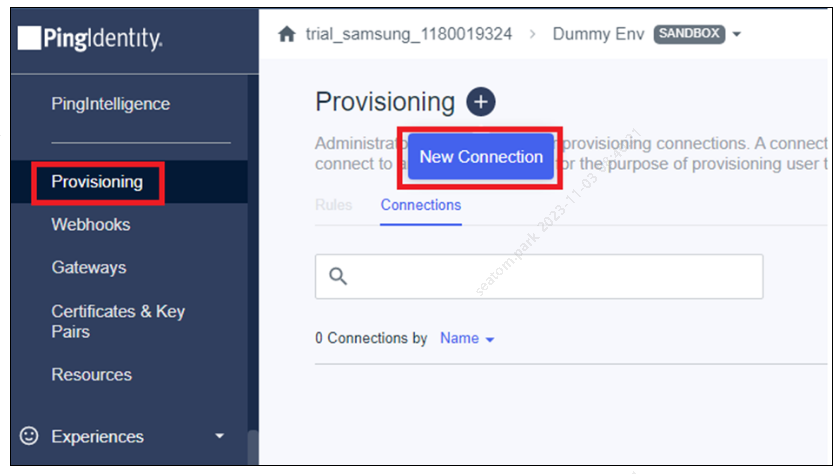
In the Ping Identity console, select Connections > Provisioning > New Connection.
-
In the connection list, select SCIM and click Next.

-
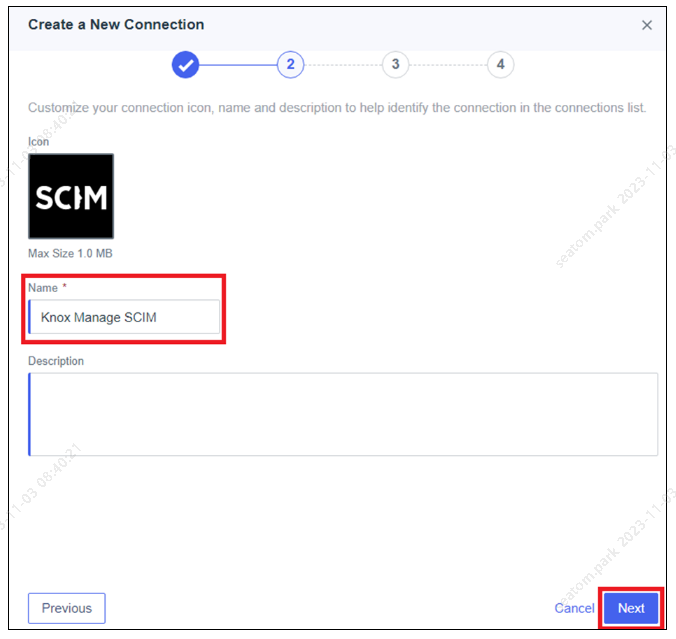
In the Create a New Connection dialog, enter Name and click Next.
-
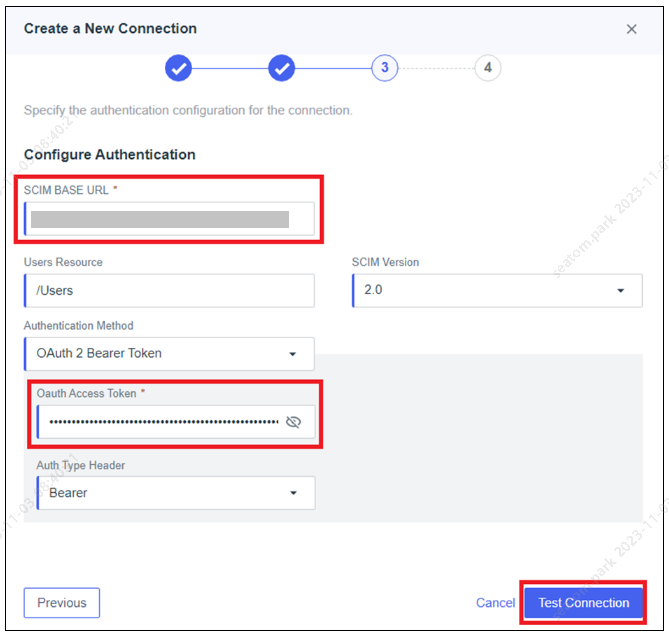
In the Configure Authentication section, set the following:
-
Set Authentication Method as OAuth 2 Bearer Token.
-
Set SCIM BASE URL as the tenant URL copied and saved earlier.
-
Set OAuth Access Token as the secret token copied and saved earlier.
-
-
Click Test Connection to validate the connection and click Continue.
If the test fails, ensure that the Tenant URL and Secret Token are correct and the connection was properly saved and try again.
-
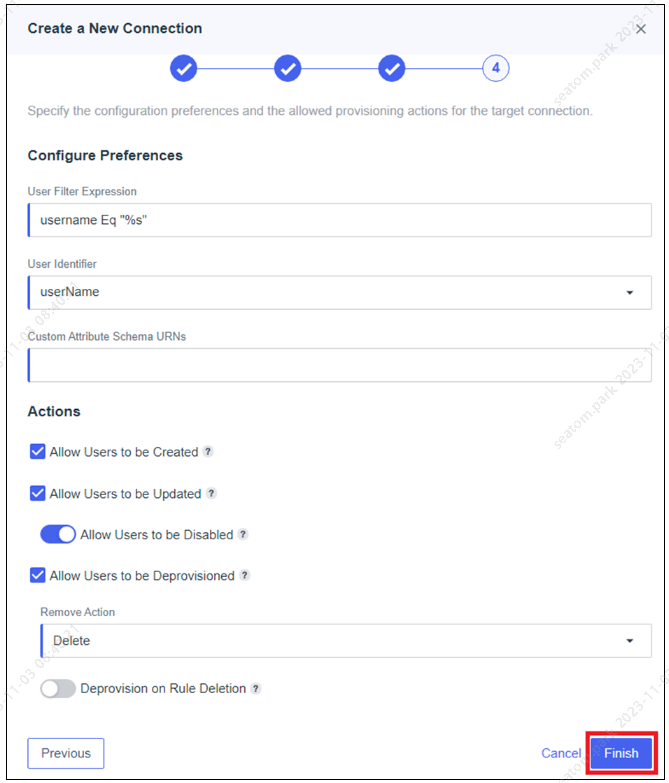
Retain the default settings defined under Configure Preferences and click Finish.
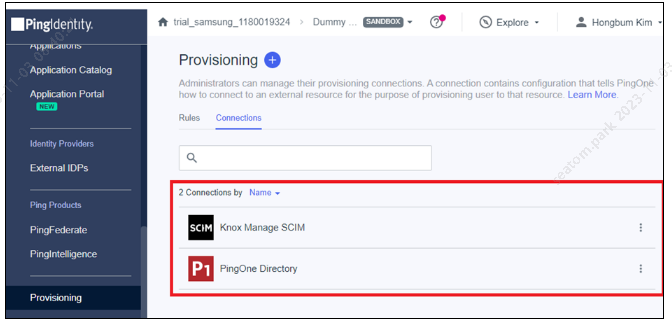
After successful connection set up, two provisioning connections are created.
Step 3 — Configure user scopes for Knox Manage in Ping Identity
-
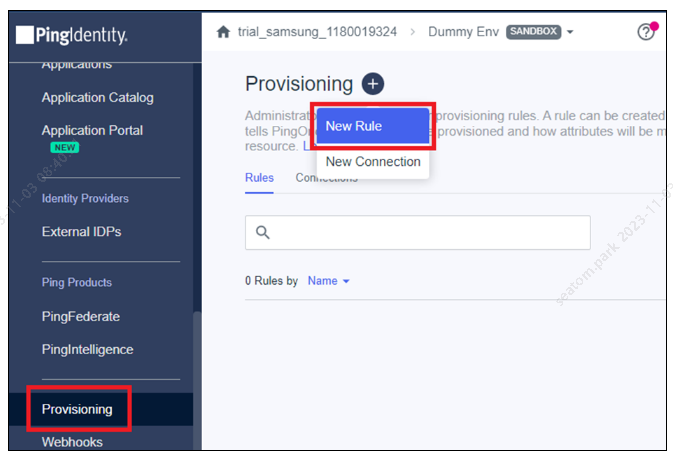
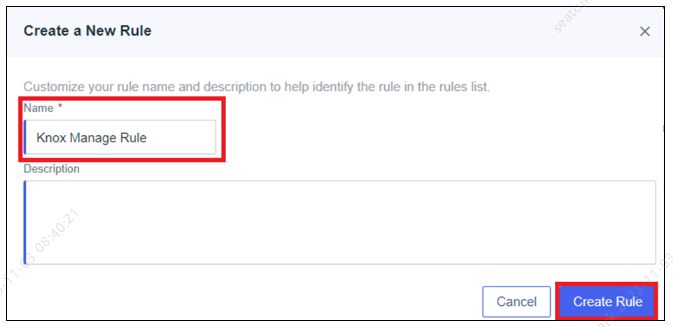
In the Ping Identity console, go to Connections > Provisioning, and click New Rule.
-
Enter the name of the rule and click Create Rule.
-
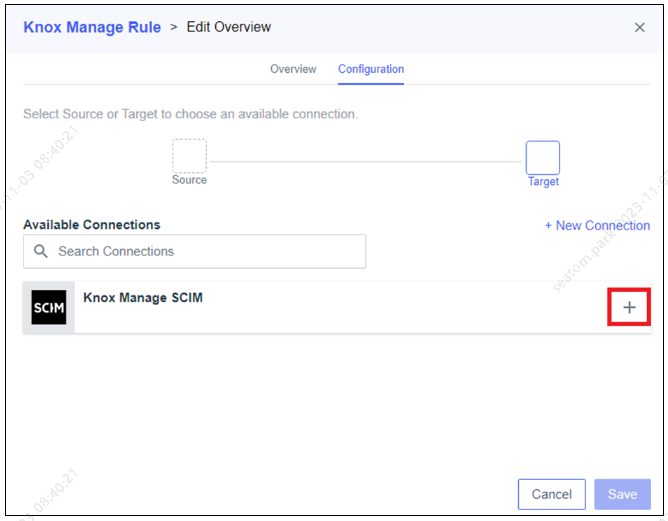
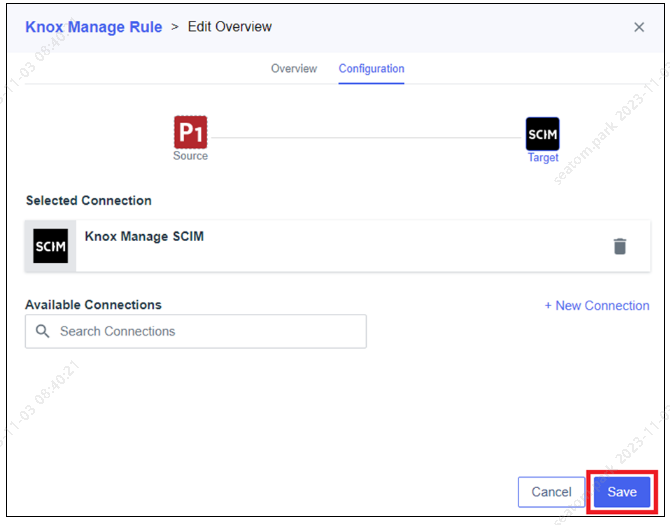
In the Configuration tab, click the plus icon to select the previously created connection, and click Save.
-
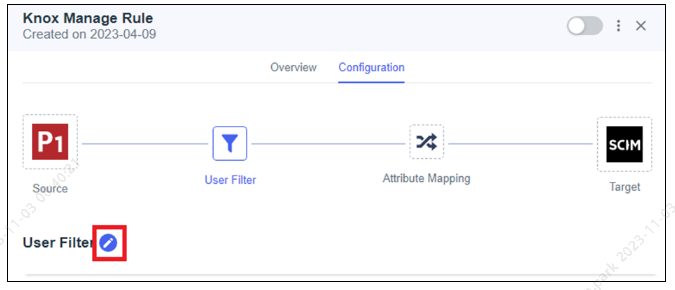
Click User Filter and specify the users to be provisioned. For example, you can specify all active users. You can use a scoping filter as described in Ping Identity’s topic Adding a user filter.
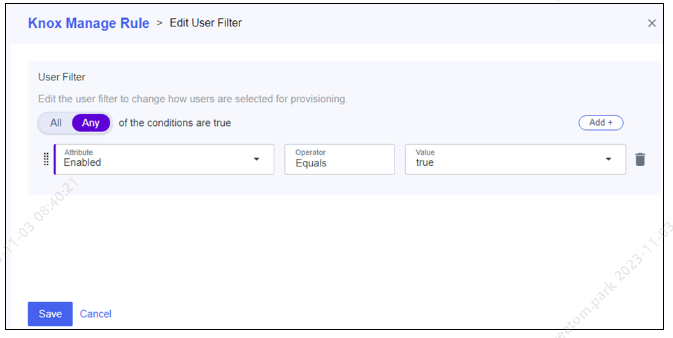
-
Click Save. The filter displays on the User Filter page.
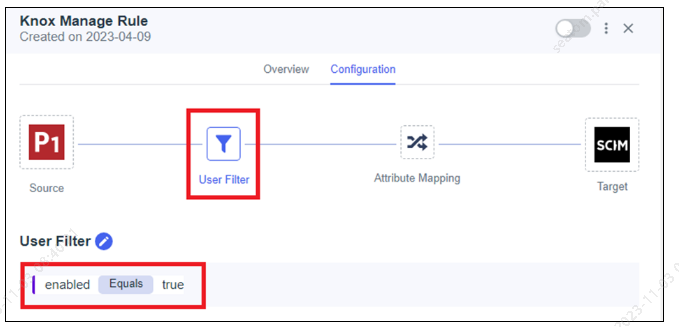
-
Go to the Attribute Mapping page and click the Edit icon.
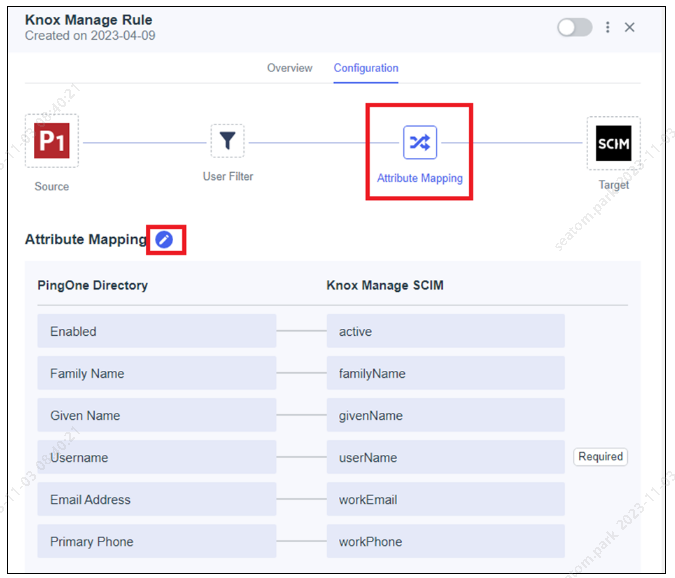
-
Click Add, map User ID from PingOne Directory to externalId in Knox Manage, and click Save.
If this mapping is not added, user sign in to Knox Manage will fail on devices.
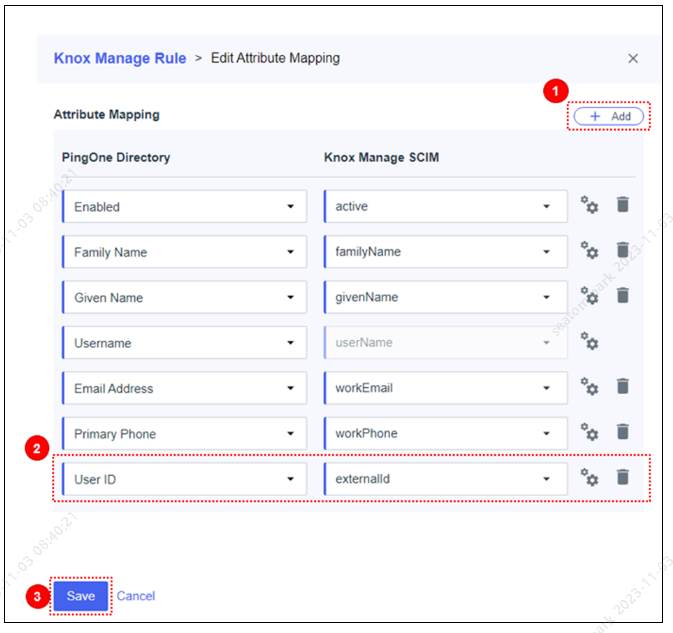
-
Enable the Knox Manage Rule using the toggle at the top of the page.
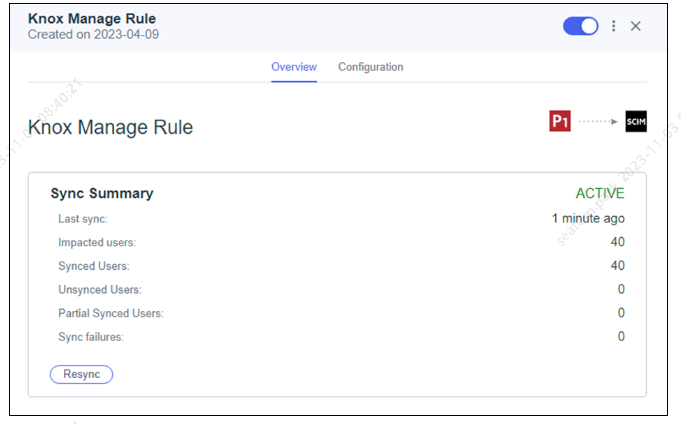
The user provisioning process starts and the sync summary report is available in the Overview tab.
For more information on how to configure the Ping Identity User Provisioning, see Configuring provisioning.
On this page
Is this page helpful?