Knox Configure 1.19 release notes
Last updated July 26th, 2023
Knox Configure (KC)
Booting animation creator now included in KC console
This enhancement enables administrators to customize boot animation by uploading images and setting the appropriate image rotation, dithering level and size. Once created and uploaded, an admin can preview and verify the animation before assigning to devices. When added into the console, the animation is available as a .qmg file for profile assignment and a MP4 file for preview within the console.
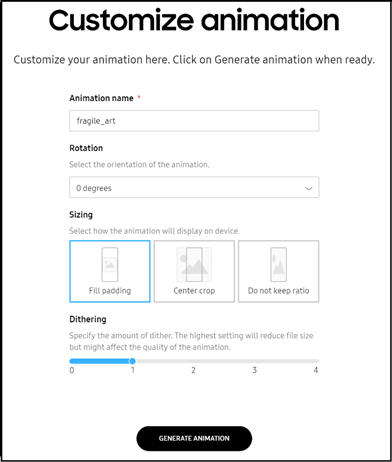
Once verified, an admin can create a profile with relevant settings and add the animation file. The admin can then push the profile to specific assigned devices and check to ensure the devices are configured properly with the animation file.
Location/GPS concept change page with Android P
With this release, the GPS option is removed from the Device connectivity section of the KC console and replaced with Location for Android P. All related APIs are deprecated. The same GPS parameters as previous will still remain within the console, but they will be changed to Location parameters.
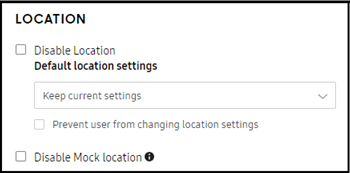
This feature is supported on Knox version 2.9 and above devices with both Setup and Dynamic edition profiles. All new KC version 1.19 profiles will have this user interface update, and previously created profiles will retain their legacy GPS settings for backward compatibility.
New email notifications for pending license expiration
This feature addresses customers reporting difficulty recovering unassigned devices due to license expiration without adequate expiration messaging. SLM license expiration warning emails are typically sent incrementally months in advance of the actual expiration date, but the email recipients may not be the appropriate admins responsible KC license administration. Therefore, with this release, KC will send email reminders to IT admins 2 months, 1 month, 2, weeks, and 1 week in advance of the license expiration date. A typical reminder email contains the license name, type, license key, license key quantity and validation period.
This new email notification enhancement is supported on both Setup and Dynamic edition KC profiles.
A new version of an existing app can also be easily updated within the profile edit page by selecting add new version.
Wi-Fi direct enrollment support added to KDA
This release introduces a new enrollment option in addition to the existing KDA Bluetooth and NFC enrollment options. Wi-Fi direct supported devices can connect directly to one another via a WLAN without joining a traditional wireless network or Wi-Fi® hotspot. Once enabled, the device automatically scans for other supported Wi-Fi direct devices. Once discovered, specific devices can be selected for enrollment data transfers.

With Wi-Fi direct, only out-of box trigger deployments are supported. Trigger deployments utilize a plus sign (+) gesture on a device’s Welcome screen to start an out-of-box deployment and bypass the setup wizard.
To utilize the Wi-Fi direct option, the receiver device must be utilizing Knox version 3.2 or above. Additionally, only Note9 and Tab S4 and above devices are supported. Wi-Fi direct is not supported on wearable devices.
KC for Wearables
Simplified wearable app (.tpk) deployment process
This feature addresses administrator requests to upload a .tpk file into the WKC console for use with wearable devices. With this enhancement, Administrators no longer need to register apps to Galaxy. A descriptive error message will display when an unsupported file format is uploaded, or if the .tpk file exceeds a specific size.
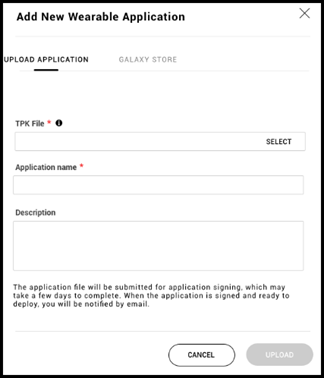
An administrator can also now add an uploaded application to a profile when in a “Ready to deploy” status. Email notification now sent to user when an application signing succeeded or failed event occurs allowing for faster response to a failed signing event.
Option added to disable NFC and restrict users from turning on/off
This feature enables an IT admin to Disable NFC and restrict device users from changing their device’s NFC settings. A tooltip is also added to convey that the device user is unable to change the NFC setting once the relevant security policy assigned by the IT admin.
On this page
Is this page helpful?