Overview
Last updated February 8th, 2024
Welcome to Samsung Knox Universal Credential Management Developer Guide. This guide provides information about how to use the Samsung Knox Universal Credential Management (UCM) APIs to develop Android™ apps that MDM providers can implement in enterprise-managed Samsung mobile devices—both on the device and inside Knox Workspaces. This guide also explains how storage vendors can create a UCM plugin which allows UCM-enabled apps to seamlessly access their storage space.
Universal Credential Management works only on Qualcomm and Exynos chip devices.
Background
Android applications are able to store digital credentials securely on Samsung Android devices using the hardware-backed Key store. Some use cases require the use of an external storage, such as a smartcard or micro SD card to store credentials. Unfortunately, each type of credential storage comes with its own proprietary APIs. Using these APIs as a direct interface complicates app development, debugging, and maintenance because the app must be customized for each vendor’s interface. This means that when a deployed app needs to access a new type of storage, or even the same type of storage but from a different vendor, the app needs a patch to call the new APIs. The Universal Credential Management (UCM) Framework aims to reduce this complexity by enabling applications to access all credential storage devices through the same set of interface, regardless of the underlying storage type. The following sections will explain the UCM Framework, how applications use the UCM APIs to access credentials and how storage vendors can integrate their solutions with UCM.
About Knox Universal Credential Management
Samsung’s Universal Credential Management (UCM) SDK provides a future-proof plug-and-play framework to ease the management of credentials across a variety of different possible storage media. The SDK uses a common set of APIs to manage credentials on many possible current and future storage options, hiding the implementation details of individual storage providers so that mobile app developers can write code once and not worry about continual app updates. In the simplest sense, the UCM framework provides the following piece to the puzzle of apps, interfaces, and storage types:
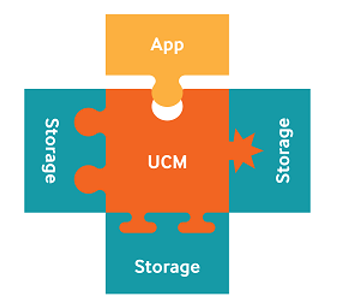
In a more complete sense, the Knox UCM presents a single interface to the independent parties who are sharing the mobile device environment and resources as shown below:
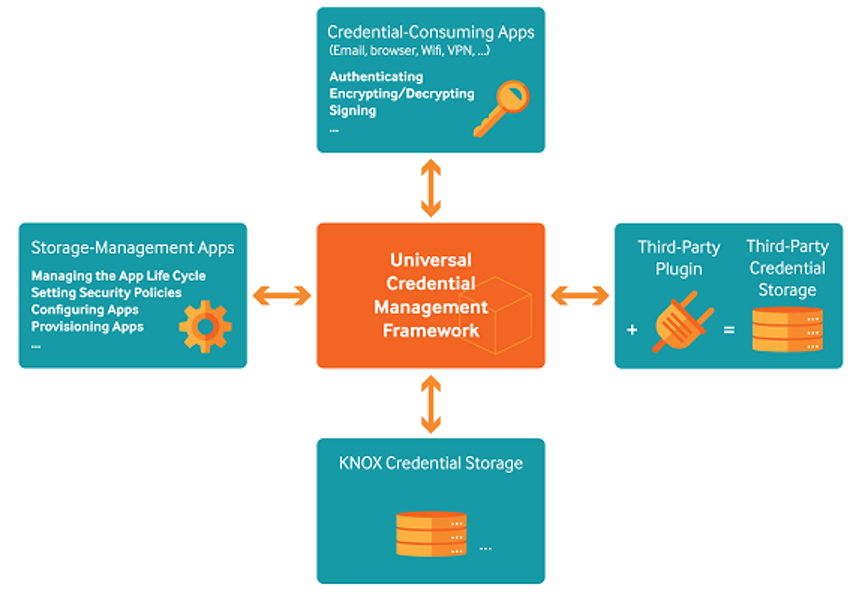
The UCM framework provides API for accessing the Smartcard facility, and UCM framework supports calls with the Java Cryptography Extension (JCE) API to access each Smartcard. Ultimately, the streamlined interface of UCM helps independent parties accomplish their tasks while bypassing the complexity of their peer’s custom API.
Who does UCM help?
Application developers
- No need to program with specific implementations for each credential storage.
- Take advantage of many different types of credential storages with minor or no code changes.
Storage vendors
- Make credential storage solutions accessible to existing applications, including Samsung native applications.
- Take advantage of extra functionality provided by UCM services layer.
- Easily integrate the Samsung UCM plugin on top of your existing Android application service using Samsung Knox.
Enterprise customers
- Enterprise systems that are already issuing smart cards and user credentials can increase the level of security for users wanting to use mobile services such as secure email, access to enterprise VPN, and enterprise web sites.
UCM feature list
UCM cryptography
Application can access the UCM features through the UCM plugin and can add it using standard JCE APIs. The application can then obtain instances of the JCE classes (KeyStore, SecureRandom, KeyPairGenerator, KeyGenerator, Signature, Mac, and Cipher) to perform cryptographic operation based on the smartcard. The UCM framework routes JCE calls to the correct UCM provider and credential storage of the plugin. The UCM framework is also integrated into the Android KeyChain, so the application may view and choose the certificate stored on the smartcard.
UCM keyguard
Android keyguard authenticates users based on their pattern, PIN, and password. The UCM framework is integrated into Keyguard, so user can use smartcard as an option for authentication. UCM keyguard is based on PIN authentication. If PIN authentication is successful, the UCM framework will retrieve the password that is generated inside smartcard, and use it as the device password.
UCM DAR (Data At Rest)
When DAR is enabled, the Credential Encrypted (CE) storage is encrypted using the File Based Encryption (FBE) master key, which is generated on the device. This encryption can be done with an FBE Master key generated by a smartcard as well.
On this page
Is this page helpful?