How the UCM framework works
Last updated February 8th, 2024
The UCM framework uses an application allowlist to control credential storage and access. UCM determines whether or not an app is legitimately authorized to access a storage space or a particular credential by checking the allowlist and the application’s UID.
Allowlisting access to credentials
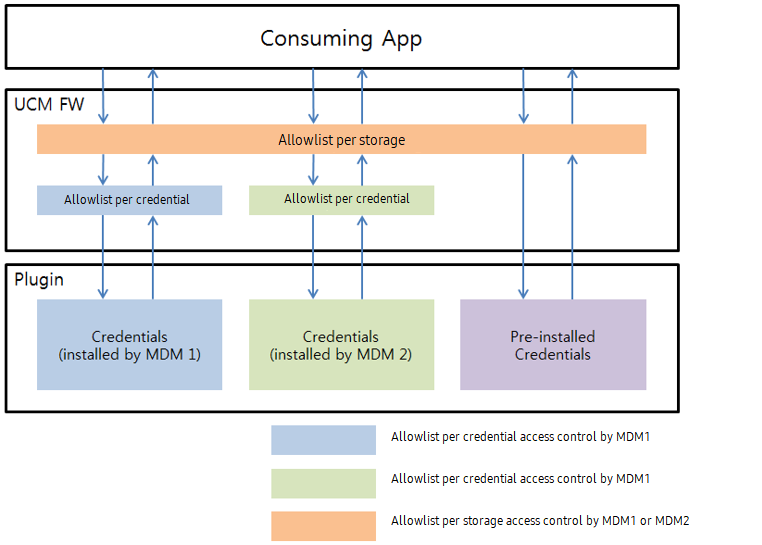
The UCM framework has two types of allowlists to access credentials:
- Allowlist per Storage — If an application is added to this allowlist, then the application can access the third-party UCM plugin that manages credentials on the third-party storage device. MDMs with the proper UCM permission can configure the allowlist exclusively.
- Allowlist per Credential — The MDM that installs the credential owns the credential and is the only one that can configure the allowlist.
Pre-installed credentials do not have an MDM installer, and cannot be managed through the Allowlist per Credential. Instead, these credentials are managed through the Allowlist per Storage.
Managing multiple users
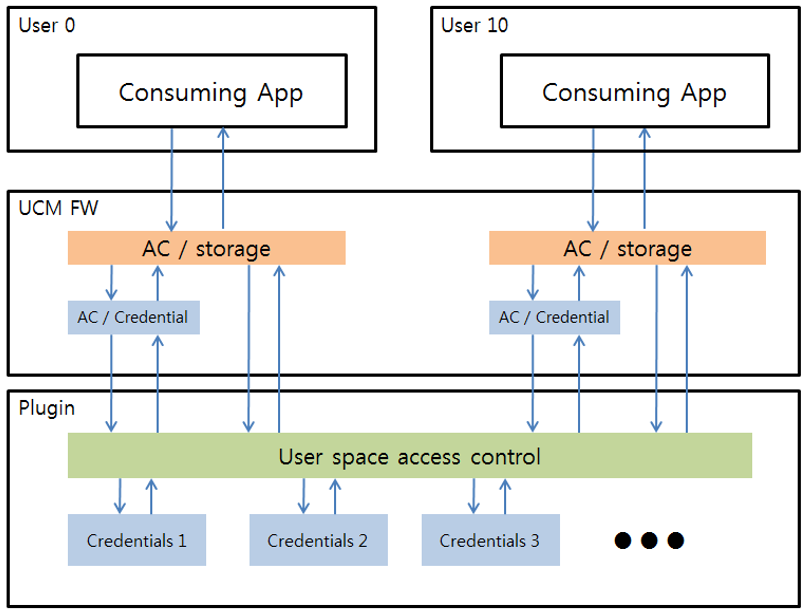
The UCM framework supports user space isolation for multiple user accounts, depending on plugin configuration. All UCM Cryptography actions involve user ID and application UID. The UCM plugin retrieves the user’s information when an MDM or 3rd party tries to install credentials. The UCM plugin can then store the credentials separately by a user and return the proper credentials. This isolated access depends on the plugin’s implementation. For more information, see Create a UCM plugin.
Handling credential requests
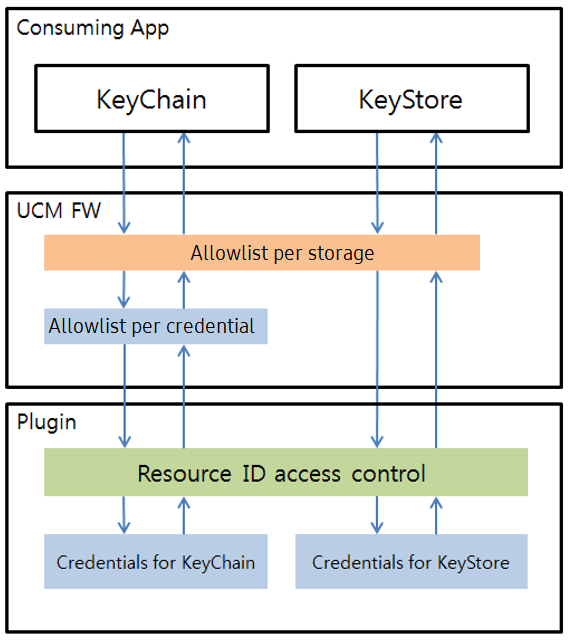
The Android KeyStore provides the following types of credential storage on Android devices:
- KeyChain — The credentials installed by KeyChain are accessible by all applications using KeyChain and KeyChainActivity.
- KeyStore — Credentials installed by KeyStore are accessible exclusively through the installer.
When an application requests credentials, the UCM framework sends a different UCM resource ID to the plugin for authentication. If the application uses:
- KeyChain — The UCM framework sends SHARED_KEYCHAIN_RESOURCE.
- KeyStore — The UCM framework sends PRIVATE_RESOURCE.
The UCM plugin then retrieves the requested credentials and sends them through the UCM framework to the requesting application.
On this page
Is this page helpful?