Extending Below-the-OS Security into the OS
Last updated August 12th, 2024
Having established a secure Below-the-OS platform, it’s critical to extend security into the OS. Several security-sensitive operations, such as logging, occur either in the OS kernel or in processes. For robust security, Below-the-OS platform components need to integrate with and protect these security-critical OS components.
Samsung Galaxy Books with the Knox security platform have special Below-the-OS security features to protect security-critical OS components from tamper, and to integrate Below-the-OS security events into Windows event logs.
Samsung Security Service Tamper Protection using Below-the-OS
Malware and ransomware often try to kill, disable, and uninstall security components such as logging services to evade detection. Therefore, it’s important to protect such services from tamper. However, protection is especially challenging since Windows malware often executes with elevated system privileges, allowing malware to easily kill and uninstall security-related services.
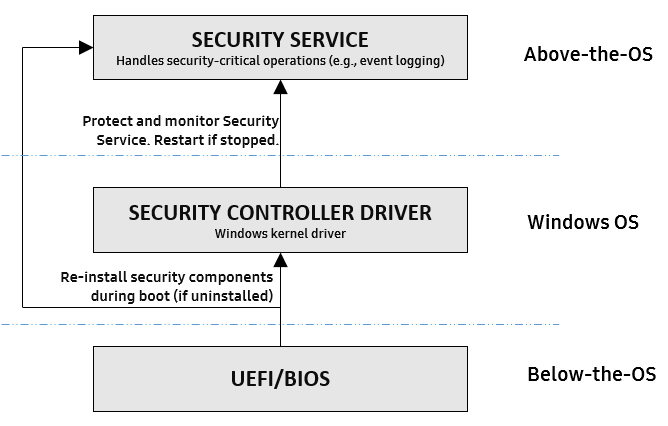
Figure 6: Samsung Security Service Tamper Protection from Below-the-OS.
Samsung’s Security Service handles critical operations such as logging. Thus, it’s important that the Samsung Security Service remains protected from tamper.
This protection begins at boot-time and extends through run-time. During boot-time, as shown in Figure 6, the UEFI and BIOS securely reinstalls Samsung’s Security Controller Driver and the Samsung Security Service if either of these are uninstalled or not present. It does this by using a standard Windows mechanism called the Windows Platform Binary Table, or WPBT, during boot. This process verifies that the security driver and service binaries are signed by Samsung before starting them.
The Security Controller Driver and Security Service binaries are embedded into the UEFI image, and are thus immune from file system tampering. At run-time, the Samsung Security Controller Driver monitors and protects the Security Service by using layered defense mechanisms. If the Security Service process is somehow stopped, the Security Controller Driver is notified through callbacks and instantly restarts the service. The Security Service binary is itself compiled with protection against run-time attacks such as code or DLL injection using various defense-in-depth techniques.
Event integration with Windows Event Viewer
Another important aspect of extending Below-the-OS security into the OS is to make sure that Below-the-OS security events are appended to existing OS logs in a secure manner. Samsung’s Below-the-OS and in-OS security components generate boot-time and runtime security events that are stored in logs in persistent and secure SPI flash memory.
The Security Service’s Event Logging Service appends these events to Windows Event Logs, which can be viewed using the Windows Event Viewer. To ensure that event logging can’t be bypassed, the Event Logging Service is started on every boot and is protected from tamper or shut-down at run-time. For more details, see Samsung Security Service Tamper Protection.
The Event Logging Service logs several types of security events and information that can be viewed using the Windows Event Viewer under a dedicated “Samsung Security” application event log section. The following events are available:
- Below-the-OS security events such as Tamper Alerts, unauthorized writes to BIOS variables and protected SMM areas, BIOS and Secure Boot key recovery attempts, and suspicious SMI calls.
- In-OS security events such as uninstalls, unloads of security-critical components such as the Security Service, and writes to security-critical registry keys.
- Security state of the system, such as the security software version information, enable/disable status of security-relevant BIOS settings, and variables such as Secure Boot, Advanced SMM Protection, SMI Guard, and TPM activation status.
Event severity levels are one of Information (normal but security-relevant events), Warning (notice of abnormal events that have been automatically resolved), and Error (unrecoverable events that need administrator action).
User notifications
When certain security-critical events happen at runtime, in addition to being logged, the user is notified of the event through a toast notification in Windows. The user has the option to obtain more information or dismiss the event, as seen in Figure 7.
Figure 7: Notification of a Tamper Alert
On this page
Is this page helpful?