Real-time Kernel Protection (RKP)
Last updated February 20th, 2024
The Knox Platform’s patented Real-time Kernel Protection (RKP) is the industry’s strongest protection against kernel threats and exploits. RKP works seamlessly out-of-the-box, with no setup required. Simply powering on a Samsung Knox device provides world-class threat protection and attack mitigation. RKP supports the rest of the Knox security offerings to provide full security coverage without the typical gaps anticipated with mobile devices.
Why does kernel protection matter?
Kernel protection is central to device security and enterprise data protection. When attackers find software vulnerabilities, they often escalate privileges and compromise the core of the OS: the kernel.
A compromised kernel can leak sensitive data and even allow remote monitoring and control of the affected device. Other more commonplace protections like Secure Boot or hardware-backed keystores are of little value if the kernel itself is controlled at runtime. After a device boots and decrypts sensitive content, a kernel compromise can result in data leaks that directly impact an enterprise’s data integrity.
RKP design and structure
As part of the Knox Platform’s security offerings, RKP employs a security monitor within an isolated execution environment. Depending on the device model, either a dedicated hypervisor or the hardware-backed secure world provided by ARM TrustZone technology provides the isolated execution environment.
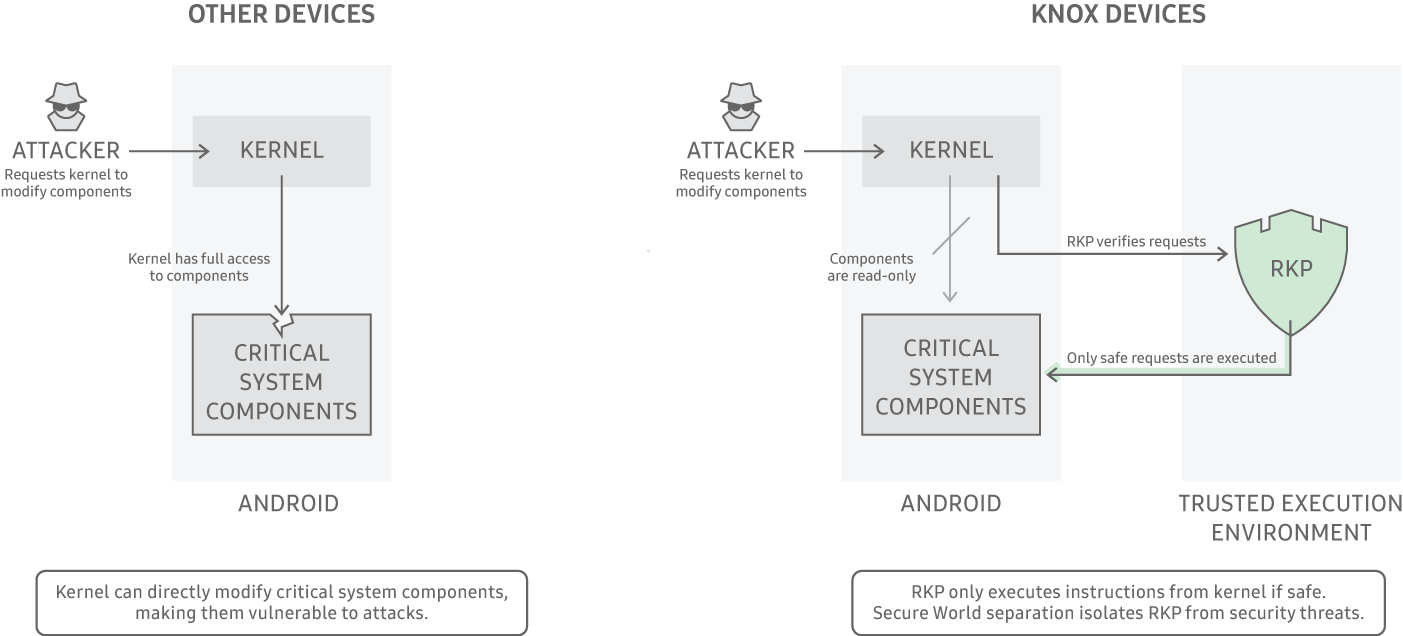
RKP’s isolation from the kernel shrinks the Trusted Computing Base (TCB) and helps secure it from attacks designed to compromise the kernel. This unique ability enables RKP to detect and prevent the most common kernel attacks. RKP protections are grouped into three areas:
- Kernel code — RKP prevents modification of kernel code and logic.
- Kernel data — RKP prevents modification of critical kernel data structures.
- Kernel control flow — RKP prevents Return-Oriented Programming (ROP) and Jump-Oriented Programming (JOP) attacks that reuse existing kernel logic to piece together exploits from the kernel’s own code.
How is kernel protection possible?
A kernel protection mechanism can’t exist completely in the kernel only, since an attacker could circumvent it if the kernel itself has a flaw. The kernel is the lowest granular control level over the OS and, as such, usually can’t be effectively monitored from any lower level in the system.
RKP uniquely employs a security monitor within an isolated execution environment. Running within an isolated execution environment would normally compromise a security mechanism’s ability to see into the kernel and monitor activities at runtime. However, RKP succeeds by utilizing patented techniques to control device memory management and by intercepting and inspecting critical kernel actions before allowing them to execute. RKP is thus able to prevent a compromised kernel from bypassing other security protections. This prevention significantly reduces the severity of kernel attacks and limits the effectiveness of exploits that would typically cripple a mobile device.
Since RKP is always active and requires no management control, kernel protection is only possible if it meets strict usability and performance requirements. RKP’s protections are activated out-of-the-box, with no performance impact to customers.
Periodic Kernel Measurement (PKM)
The TrustZone-based Integrity Measurement Architecture (TIMA) architecture provides a number of core features to protect against mobile device compromise. One of these central TIMA features is Periodic Kernel Measurement (PKM).
PKM periodically monitors the kernel to detect if legitimate kernel code and data were modified maliciously. PKM also monitors the key SE for Android data structures in OS kernel memory to prevent malicious attacks from corrupting and potentially disabling SE for Android. PKM protects the Linux kernel code and data pages from malicious exploits and helps prevent attacks attempting to disable SE for Android.
During a device firmware build, the SHA1 hash of every kernel code, and read-only data page, is calculated and gathered into a measurement file. These measurements are signed by Samsung to ensure data integrity and authenticity before it’s included in the firmware. When TIMA is initialized, PKM receives the kernel page measurements and verifies the signature to prove integrity and authenticity before storing the measurements in the secure world. During device operation, TIMA periodically recalculates the measurements of the running kernel and compares them to the signed measurements stored on the device. If any discrepancy is detected, a violation is reported to both system logs and the user.
When PKM runs, it reads the physical memory addresses used by SE for Android to determine whether:
• SE for Android is enabled
• SE for Android is in enforcing mode.
If malicious code manages to disable SE for Android, or switch it to permissive mode, PKM detects the state change and reports a violation to quickly assist an administrator in problem diagnoses.
Full security coverage
Each year, Samsung’s research and development teams add the latest runtime protections to a growing list of unique capabilities found only within RKP. At a 2018 mobile security conference, RKP was touted as the best Android protection technology available and was credited with the lack of new public exploits in the past year for Samsung Knox devices.
Although RKP is only one piece of Samsung’s holistic security solution, it successfully demonstrates the unique security guarantees possible when combining hardware, software, and advanced security research. Ensuring security claims are low maintenance, highly effective, and industry-leading is what provides enterprise customers the trust they need to deploy mobile devices in high-security environments.
On this page
Is this page helpful?