Network Platform Analytics (NPA)
Last updated February 20th, 2024
Endpoint devices, such as mobile devices, are hard to monitor for security issues. Third-party apps can’t inspect OS behaviors and networking patterns, something that is possible on desktop platforms. These limitations, combined with the prevalent use of endpoint encryption create an information “black hole”. This information black hole makes it more difficult to detect misconfigurations, troubling network usage patterns, the misuse of enterprise resources, or other signs of issues that impact an enterprise’s bottom line.
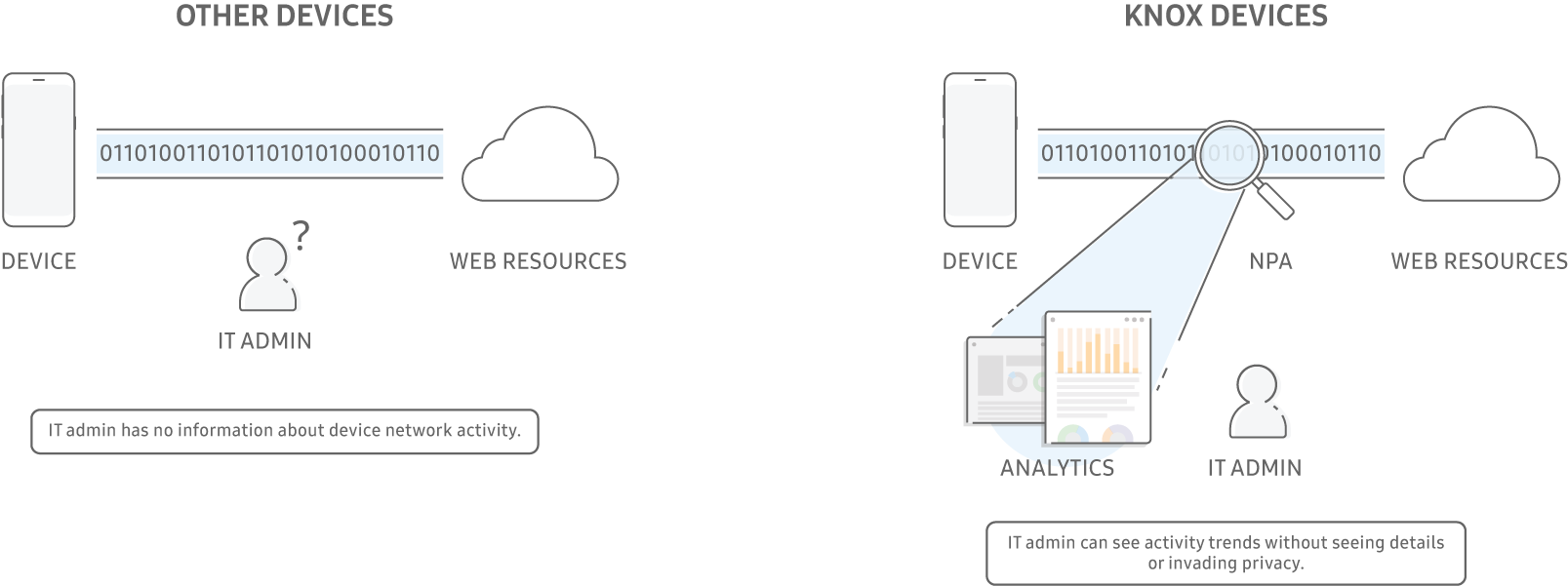
The NPA framework enables insights into mobile software and network use, misconfiguration, and network-based threats. Powerful analytics solutions use the NPA framework to increase endpoint visibility without violating the confidentiality of data moving across enterprise devices and networks.
Combined with a compatible analytics solution, NPA simplifies many device administration tasks:
- Detect more IT problems — “I don’t know what I can’t see!”
- Detect problems faster — “Notify me automatically of suspicious patterns.”
- Investigate more easily — “Walk me through the chain of events.”
- See root cause attribution — “Am I being attacked? Is this a bug? Is something misconfigured?”
- Provide visibility required to trust mobile devices — “Show me how my network is being used.”
- Enable quicker remediation — “Lock down the device, user, or app causing this issue!”
NPA design
The NPA framework provides real-time information about the network packets leaving a device and the context surrounding the flow of data. An NPA-compatible Network Analyzer then analyzes the available data to provide valuable insights. Is your new beta app sending sensitive data to an unexpected server in a foreign country? Analyzing endpoint flow data gives us insights into network traffic, such as:
- The destination of every network flow, using either IPv4 or IPv6 addresses
- The domain name originator associated with the destination IP address
- The start and stop time for the network flow
- The number of bytes transferred in and out during the network session
- The name of the process or app initiating the data flow
- The cryptographic signature of the app initiating the data flow, and of its parent process
- Whether or not traffic originated from a tethered device (for example, a mobile hotspot) or from within the device
NPA maintains enterprise data confidentiality as it only inspects the header data and the context surrounding network traffic patterns. NPA and NPA-compatible network analyzers don’t have access to actual data packets. This feature is a strong differentiator compared to solutions that unnecessarily collect and redirect all endpoint network traffic, usually by means of a web proxy or VPN.
Unique advantages of Knox NPA
The Knox platform NPA provides the only mobile platform for granular endpoint networking insights. Some unique advantages are:
- NPA is unaffected by endpoint network encryption.
- NPA can uniquely attribute network patterns to the specific software responsible.
- NPA can differentiate between traffic originating from a well-known Android app and a fake app impersonating the app.
- NPA does not expose your entire network traffic to the analytics solution.
NPA-compatible solutions
Samsung’s release partner for NPA is Cisco. Cisco’s network security products can now interface with Knox NPA to provide endpoint visibility of Knox devices. Admins can get this visibility even when a VPN is encrypting endpoint traffic. These insights are exposed to admins using the Cisco StealthWatch console and remediation steps performed using Cisco ICE.
Other Knox partners are preparing NPA-based solutions to help solve other common problems associated with mobile device deployments.
On this page
Is this page helpful?