Configure SSO settings
Last updated March 24th, 2023
The Knox Partner Portal can be set up for use with several identity management providers. See below for detailed steps on how to integrate Knox Partner services with your specific provider.
- Configure Microsoft Azure AD SSO settings
- Configure Ping Identity SSO settings
- Configure Okta SSO settings
Note
If you enable SSO as a sign-in method, you cannot use your Samsung Account to sign in to Knox services.
Configure Microsoft Azure AD SSO settings
On the Microsoft Azure portal
Add the Samsung Knox and Business Services app:
-
Under Azure services, click Azure Active Directory.
-
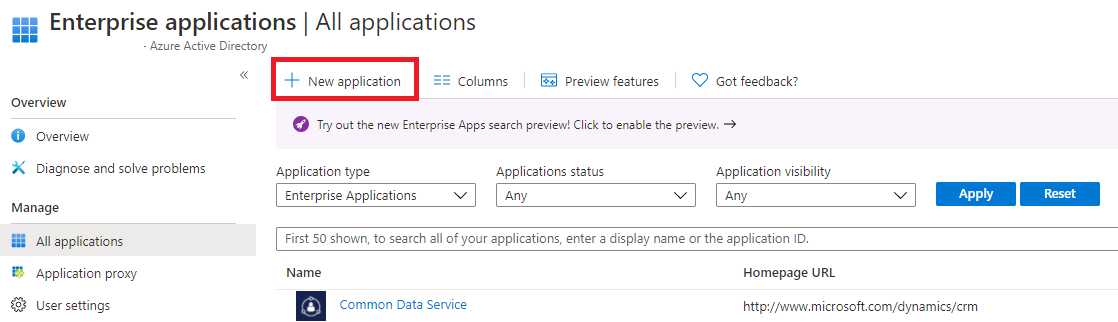
In the left sidebar, click Enterprise Applications.
-
Select New application.
-
In the Browse Azure AD Gallery section, enter Samsung Knox and Business Services in the search box.
-
Select the Samsung Knox and Business Services app from the results and add it.
Then, assign users and groups to the Samsung Knox and Business Services app:
-
In the left sidebar, click Users and groups.
-
Click Add user/group.
-
On the Add Assignment screen, under Users and groups, click None Selected.
In the list of users and groups, search for and select the users and groups to assign to the app. Then, click Select.
Note
Selected users must have an Azure Active Directory account.
-
At the bottom of the screen, click Assign to allow the users to access the app.
-
Connect to AD SSO
Finally, follow the steps below to set up the Basic SAML configuration:
-
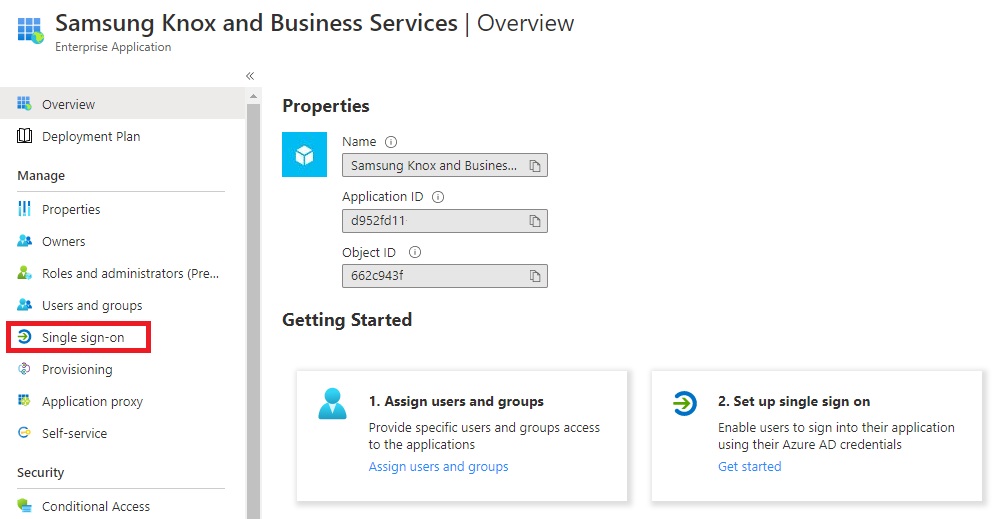
On the Azure portal, select the Samsung Knox and Business Services application page, navigate to the Manage section and select Single sign-on.
-
Select SAML as the single sign-on method.
-
Under Basic SAML Configuration:
-
For the Identifier (entity ID) field, enter https://www.samsungknox.com/.
-
For the Reply URL (assertion consumer service URL) field, enter https://central.samsungknox.com/ams/ad/saml/acs.
-
For the Sign on URL field, enter https://accounts.samsung.com/.
-
-
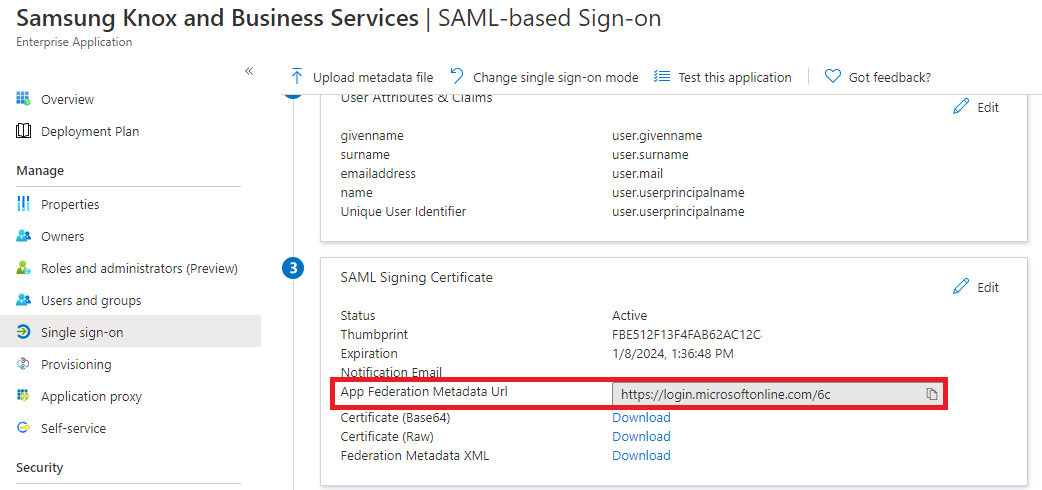
Under SAML Signing Certificate, copy the App federation metadata URL.
-
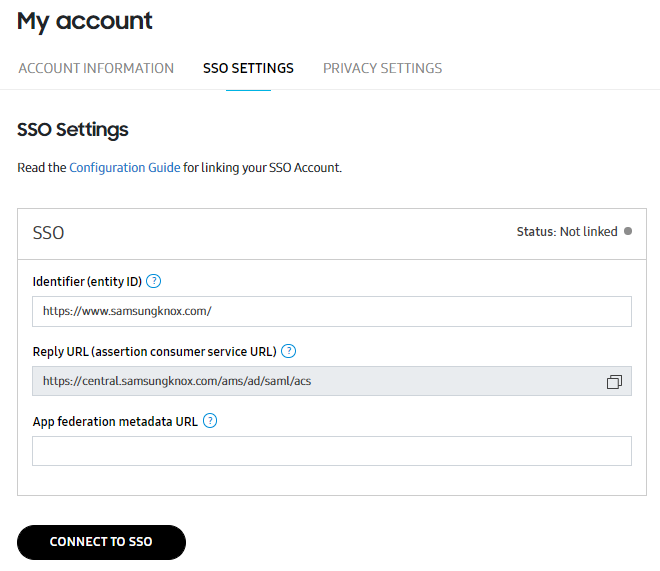
Navigate to the Knox Partner Portal. Click your account icon > My account. On the account settings page, click SSO SETTINGS. Under App federation metadata URL, paste the value you copied in Step 4.
-
Click CONNECT TO SSO.
-
In the AD sign-in window that appears, enter your AD credentials.
Configure Ping Identity SSO settings
On the Ping Identity portal
-
In the left sidebar, click Connections, then Applications.
-
Click Add Application.
-
Under SELECT AN APPLICATION TYPE, select WEB APP. In the prompt that appears, next to SAML, click Configure.
-
On the Create App Profile screen, enter the following information:
-
APPLICATION NAME — Samsung Knox and Business Services
-
DESCRIPTION — Samsung Knox is a comprehensive suite of enterprise solutions for security, manageability, and productivity.
Then, click Next.
-
-
On the Configure SAML Connection screen, under PROVIDE APP METADATA, select Manually Enter.
-
Under ACS URLS, enter https://central.samsungknox.com/ams/ad/saml/acs.
-
Under ENTITY ID, enter https://www.samsungknox.com/.
-
Under Assertion validity duration, enter 60 seconds, then click Save and Continue.
-
For PingOne users — on the Attribute Mapping screen, under SAML ATTRIBUTES, click ADD ATTRIBUTE > PingOne Attribute. Then, enter the following information in the new attribute:
-
PINGONE USER ATTRIBUTE — Email Address
-
APPLICATION ATTRIBUTE — http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name.
-
Select the Required checkbox.
For PingFederate users — add a new attribute for Email Address and map it to the following application attribute: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
-
-
Then, click Save and Close.
-
On the Applications screen, locate the Samsung Knox and Business Services item and click the toggle to enable it.
-
Expand the application details and click Configuration. Note the IDP METADATA URL for later.
Connect to Ping Identity SSO
-
Navigate to the Knox Partner Portal. Click your account icon > My account. On the account settings page, click SSO SETTINGS. Under App federation metadata URL, paste the IDP METADATA URL value you copied in Step 12.

-
Click CONNECT TO SSO.
-
In the sign-in window that appears, enter your Ping Identity credentials.
Configure Okta SSO settings
On the Okta portal
First, you need to add the Samsung Knox and Business Services application to your Okta Admin Dashboard. To do so:
-
Sign in to your Okta Administrator Dashboard. In the left sidebar, click Applications.
-
On the Applications screen, click Browse App Catalog.
-
In the search bar, enter Samsung Knox and Business Services.
-
Click the Samsung Knox and Business Services app, then click Add.
-
Once the Samsung Knox and Business Services app is added to your Dashboard:
-
Assign your user to the app.
-
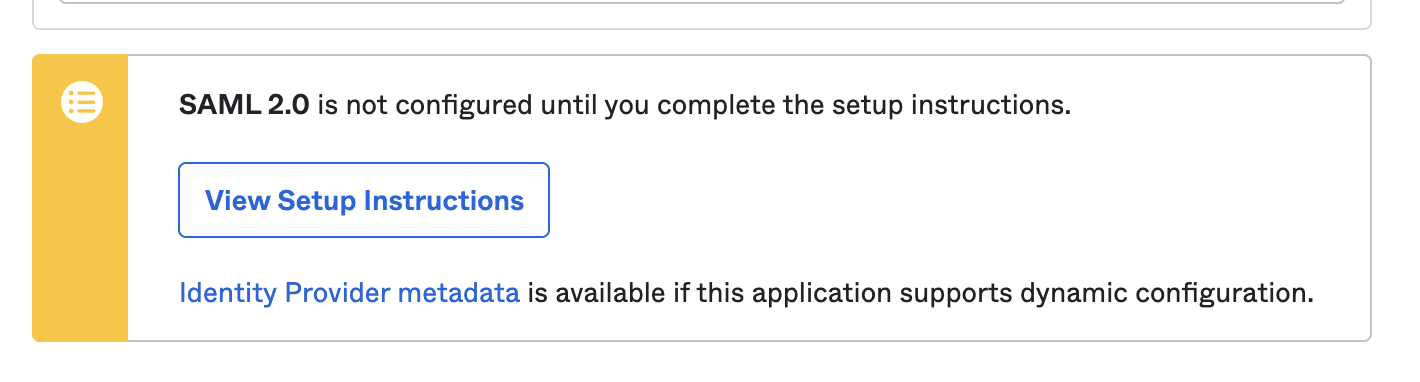
Under the Sign on tab, right-click the Identity Provider metadata link and copy it.
-
Connect to Okta SSO
-
On the Knox dashboard, click your account icon. Then, in the left sidebar, click SSO SETTINGS.
-
Navigate to the Knox Partner Portal. Click your account icon > My account. On the account settings page, click SSO SETTINGS. Under App federation metadata URL, paste the Identity Provider metadata link you copied from your Okta Admin Dashboard.

-
Click CONNECT TO SSO.
-
In the sign-in window that appears, enter your Okta credentials.
On this page
Is this page helpful?