Real-time Kernel Protection
Last updated March 7th, 2025
Kernel protection is critical for device security and enterprise data protection. Software vulnerabilities get exploited by attackers to escalate privileges, leading to kernel-level compromises that jeopardize the integrity of the OS.
A compromised kernel can significantly impact enterprise data and security due to the following issues:
- Sensitive data leak.
- Remote monitoring and controlling of affected device.
- Hardware security protections such as Secure Boot and hardware-backed keystores become ineffective when the kernel is compromised at runtime.
Samsung Knox Platform’s patented Real-time Kernel Protection (RKP) is an industry’s leading security feature designed to protect against kernel threats and exploits. It is an out-of-the-box solution enabled by default on all Knox devices, requiring no additional setup. It operates seamlessly, and enhances device performance without impacting customer experience.
When a Samsung Knox device powers on, RKP provides real-time threat detection and attack mitigation to safeguard the kernel. It also supports the rest of the Knox security features, ensuring full security coverage at runtime.
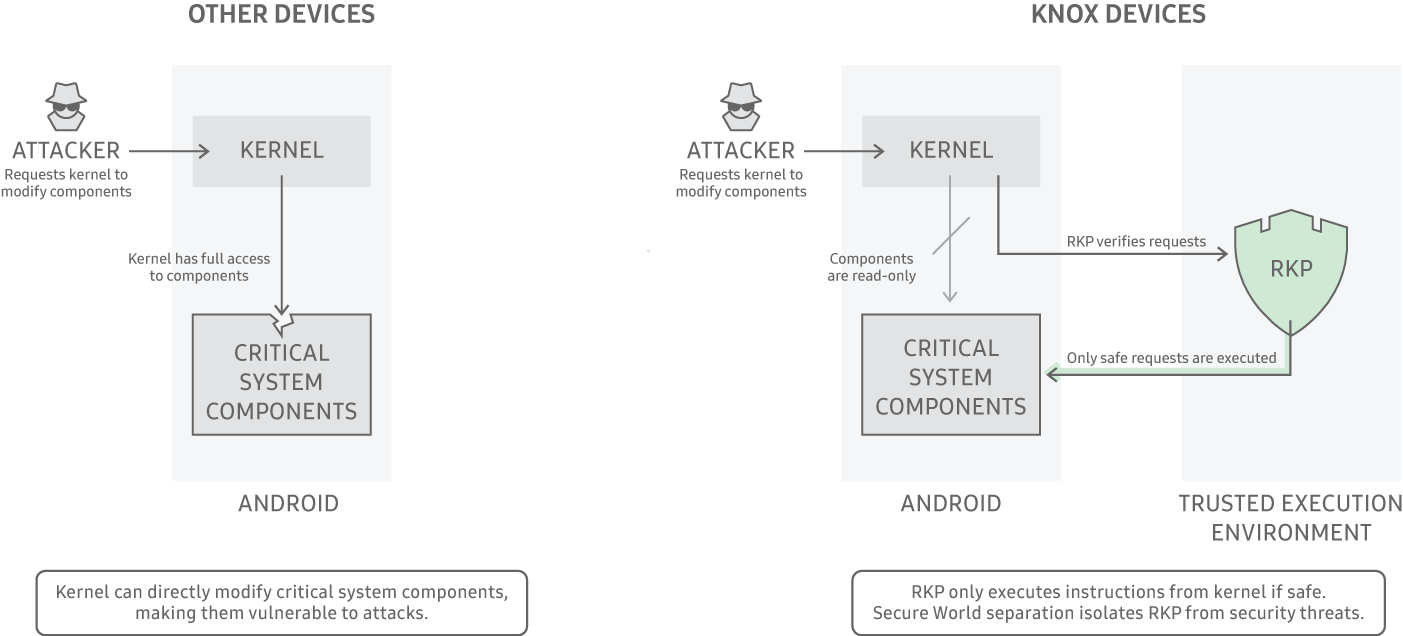
How RKP works
RKP uses a security monitor running in an isolated execution environment. This ensures the kernel protection mechanism doesn’t exist in the kernel itself, reducing the risk of circumvention by attackers exploiting kernel vulnerabilities.
The kernel operates at the lowest granular level of the OS, hence conventional security solutions can’t effectively monitor it. RKP overcomes this limitation by using the following patented techniques:
- Control device memory management.
- Intercept and inspect critical kernel actions before execution.
Due to these, a compromised kernel can’t bypass traditional security protections, and the exploit impact is significantly reduced.
On this page
Is this page helpful?